If you are an OSINT investigator you undoubtedly have your cache of tools and search resources. There is no short supply of start.me pages and link collections out there. However, for good operational security and case management a good virtual machine is just as vital to your investigation.
For the last several years Michael Bazzell and David Wescott’s Buscador VM was my go to for this, however since that project is no longer updated I’ve changed my strategy a bit. Luckily there are still several free options out there pre-configured and pre-loaded with tools that can help you get up and running quickly. We’ll do a quick tour of several of my favorites and I’ll try to leave you with enough resources you can build out your own custom virtual machine. The latter isn’t the fastest or easiest but will probably give you the best environment since you the investigator know what tools you consider a must have and which ones you would use from time to time.
To try a virtual machine out, you may not always want to grab a 20 gigabyte image file for a test drive… so I did it for you! Let’s take a quick tour!
Pre-built VM
Trace Labs Virtual Machine
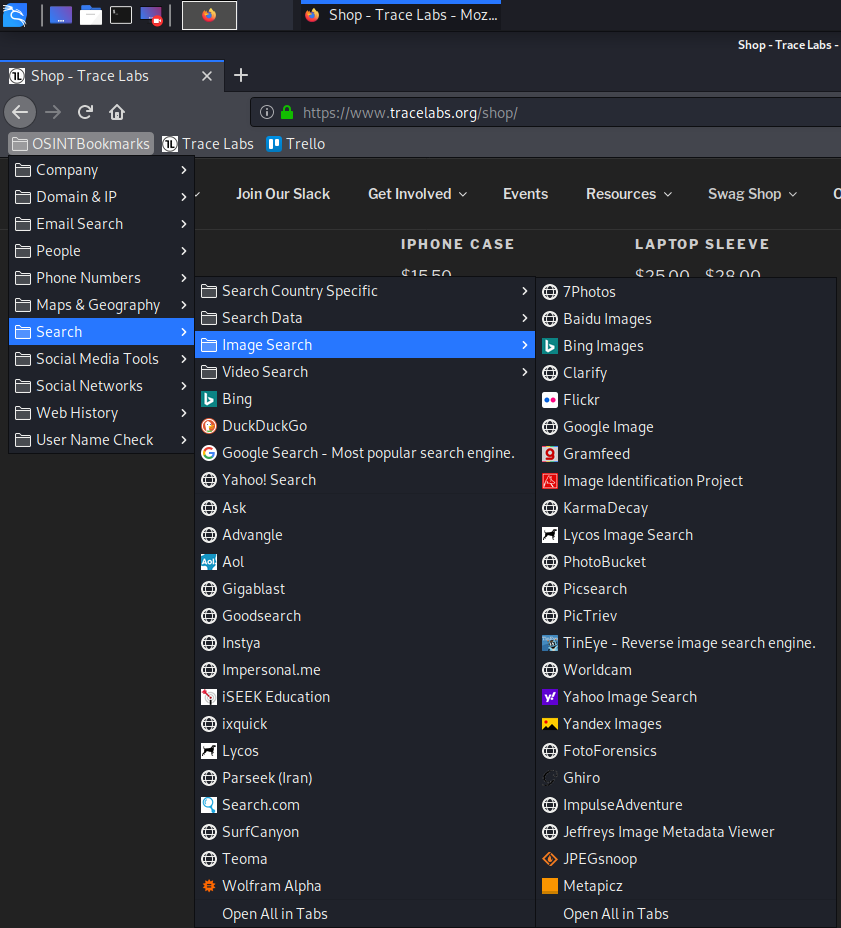
Trace Labs produced their own custom VM for anyone who may be participating in one of the OSINT Search Party CTFs. The system is a customized Kali Linux build so if you are familiar with the famous penetration testing VM you may have an extra comfort level. There were several pre-built apps and a massive OSINT bookmarks section installed in Firefox.
Nice assortment of links sorted by category
Anbox (Android in a Box) a containerized android system seemed convenient to have pre-installed, as mobile emulators can sometimes be frustrating to setup quickly.
Anbox (Android in a Box)
Other cool programs like Phone Infoga were also ready to go. If you don’t know Phone Infoga has some phone number research mixed with google dorks which opens up across multiple tabs for some fast OSINT.
Sample of Phone Infoga’s Google-fu
Those were two of the most handy pre-loads I found but there is a lot more to unpack the full list of applications in the build can be found on the Trace Labs Github page: https://github.com/tracelabs/tlosint-live#applications-included-in-the-build
With that many features the Tracelabs VM is likely an easy starting point for many researchers. The project is also on version 2.0 and seems to have some community momentum so the potential for it to improve is high.
Trace Labs VM is available for download here: https://www.tracelabs.org/trace-labs-osint-vm/
Tsurugi Linux
Tsurugi Linux is a hybrid VM designed for digital forensics, malware analysis and OSINT. I’ve used it a couple times when it first came out but they’ve released a few updates, so I grabbed a fresh copy for a look.
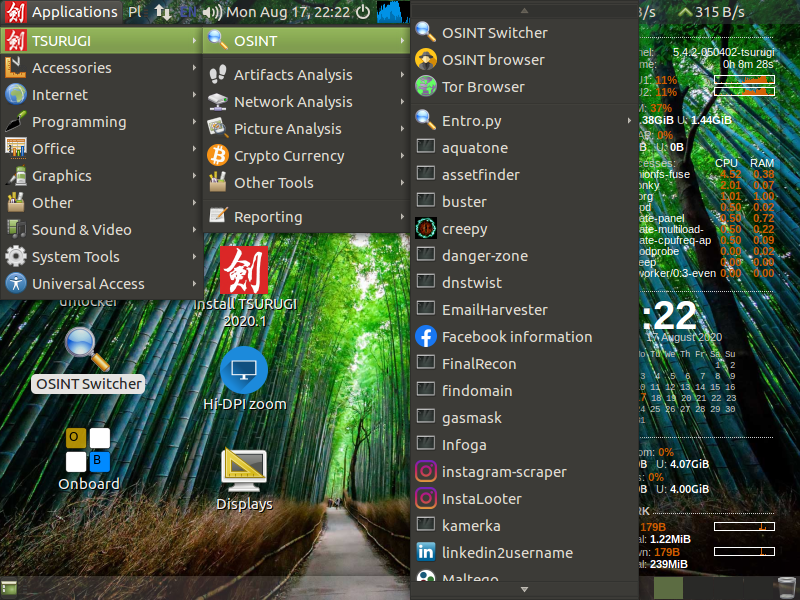
As I poked around the tools and features of the OS it is quickly apparent this VM is loaded.
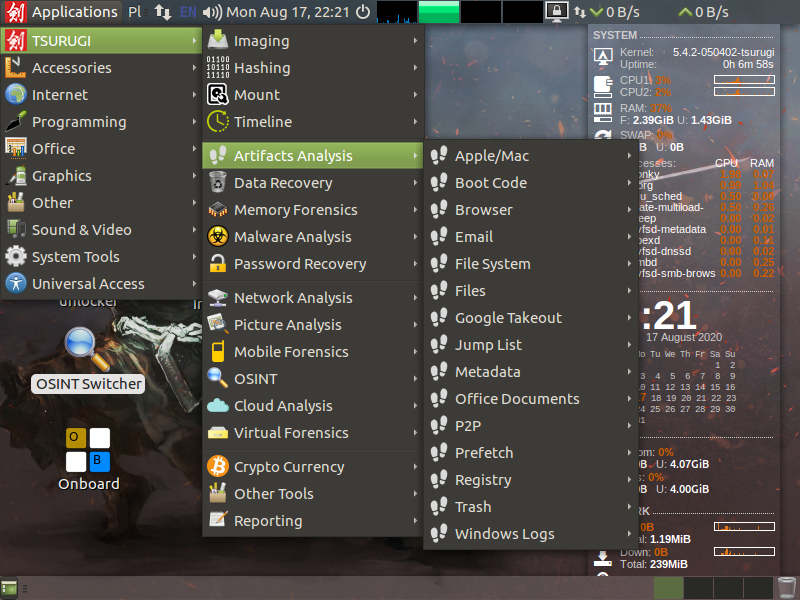
The preloaded applications for malware analysis and digital forensics are impressive, but there is an OSINT switcher that toggles many of those away for better access to the other more commonly used OSINT tools.
OSINT Switcher toggled
As I explored the OSINT tools one thing that stands out to me about the Tsurugi toolsets is that really seemed to be catered to actual analysis of data, not just collection and pivoting. There are several options for analysis of photos, video files, website structure and one of the most important sections that should never be overlooked… reporting.
If you find yourself doing specialized investigation (Digital Forensics or Malware Analysis) then you should definitely grab the latest copy for your tool kit.
Tsurugi can be downloaded here: https://tsurugi-linux.org/downloads.php
Tails
I’m counting Tails as a virtual machine for this blog, but Tails is a self-contained (on USB drive) privacy centered operating system. If I was somewhere away from my own machines or office but had access to a Tails USB drive and somebody else’s computer I could use Tails to conduct an investigation without risk of contaminating the host system. Kind of a quick and dirty solution, but one to know about. The setup goes through a bit of a process to ensure a clean install so it can take a while to setup initially.
Tails can be downloaded here: https://tails.boum.org/install/index.en.html
Remnux + SIFT
Remnux recently had an update so if you happen across anything malware related in your OSINT cases this is a good VM to know about. The documentation page found here is very useful and has a rundown of the tools and uses found in the virtual machine.
I’ve used a hybrid VM in the past that coupled the more digital forensics focused SIFT workstation. Lenny Zeltser wrote a blog earlier this month showing a few options to make the hybrid VM.
Making the hybrid VM takes a little work, but the documentation out there is great so It is pretty easy for most to follow along even if not an expert in virtual machines.
You can download Remnux here: https://docs.remnux.org/install-distro/get-virtual-appliance
You can download SIFT here: https://digital-forensics.sans.org/community/downloads
Roll Your Own
There are several free options to get ‘clean’ operating systems and bake in your own tools and configurations. Let’s face it each of us has our own investigative methods and patterns so building out your own system is not going to be the easiest answer but you may be able to keep handy the best tools for both investigating, note taking and reporting if you build out your own research VM. Below you will find a few links that may help you get started:
Ubuntu Linux
https://ubuntu.com/download/desktop
Windows 10
https://developer.microsoft.com/en-us/windows/downloads/virtual-machines/
Genymotion Android Emulator (Personal Edition)
https://www.genymotion.com/fun-zone/
My good friends at The OSINTcurious Project reminded me that our own Nixintel wrote a great blog series about building your own custom VM
https://nixintel.info/linux/build-your-own-custom-osint-machine-diy-buscador-part-1/
If you have any VM suggestions to share or comments please drop me a line on Twitter @baywolf88
Happy OSINTing